ARIC Network Defense System
ARIC Network Defense System
SIEM – Security Information and Event Management SIEM in the ARIC NDS ecosystem was created in 2003.
The system, using an intuitive graphical interface, allows you to start working very quickly right after installation.
Threats to business continuity come from many sources and are directed at various goals. Among others:
While the goal of security solutions is to detect and prevent such threats, no network can be completely secure against all of them. For this reason, SIEM itself focuses on mitigating risk, identifying vulnerabilities, detecting threats, and prioritizing responses to threats and vulnerabilities of the highest severity.
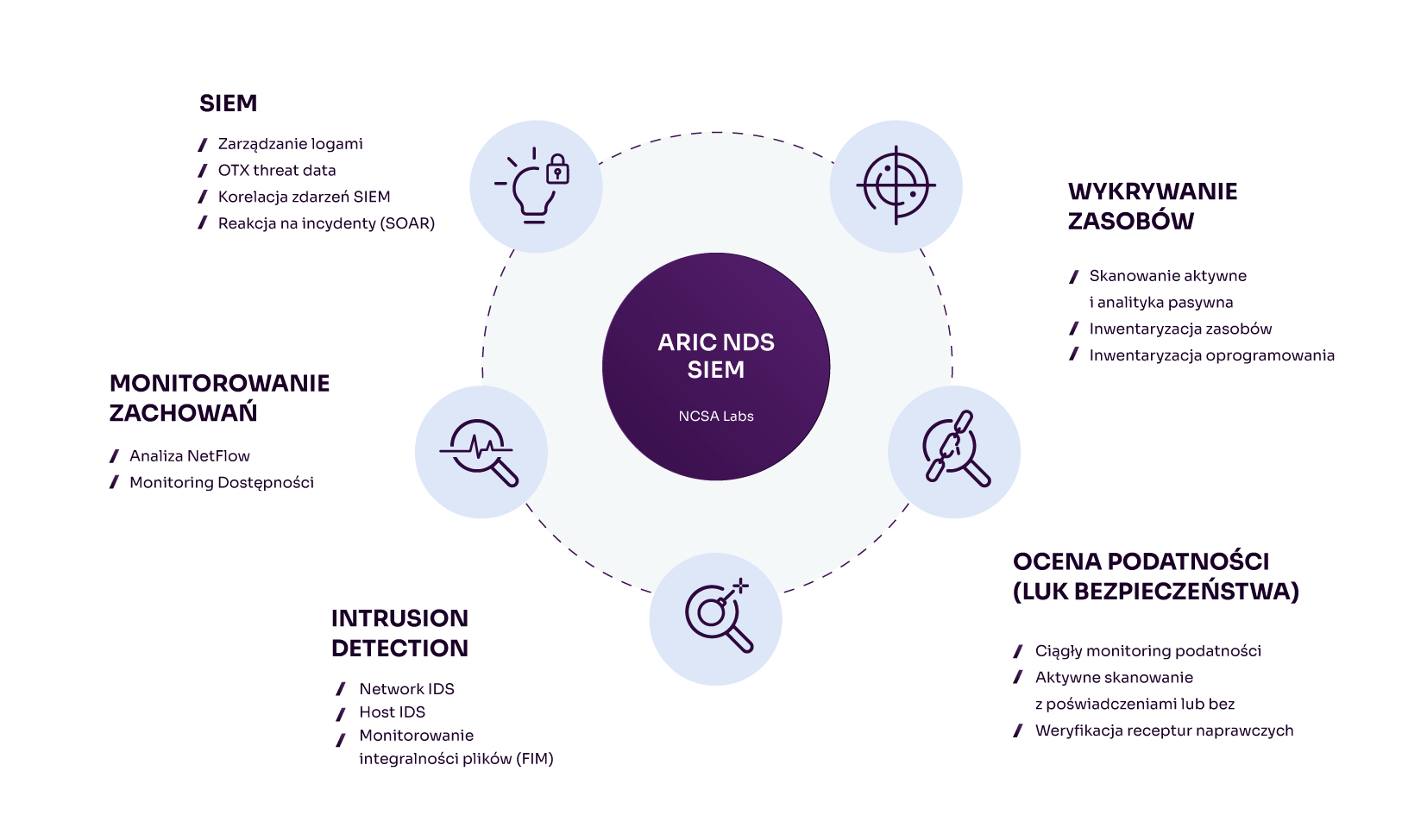
Risk mitigation, vulnerability identification and threat detection measures include:
Risk assessment
To properly secure your infrastructure, first conduct a risk assessment of your assets. Risk assessment helps determine the relative importance of resources in the network, the vulnerability of those resources to specific operational hazards, and the likelihood of incidents related to the security of those resources.
Strong security policies focus on how to best protect your most important and at-risk assets. For example, if a network resource is critical and the likelihood of an attack on it is high, focus your efforts on creating security policies to monitor such attacks and develop plans to respond to them.
Once these analyzes are performed, security policies can be designed in response to the relative asset value and exploitation risk posed by various threats and vulnerabilities. A special environment is industry (OT) and control systems, including I&C (ICS – Industrial Control System). Reference model – IACS (Purdue Model) shows layered dependencies and properly arranged architecture of the industrial environment.
Unfortunately, most industrial environments, already at the level of architecture and technological compatibility of individual products, significantly influence the automatic materialization of reams, which we observe in everyday work and qualify them as faults and failures.
Most threats in OT come from the suppliers themselves and the companies operating the delivered industrial systems. The SIEM system (regardless of the manufacturer) helps in identifying threats, but the input data must be properly prepared and, at the architecture level, the resistance of individual components and their systems to anomalies must be increased.
Correct network architecture significantly reduces environmental vulnerabilities and limits threats. For this reason, DNC series network devices (switches, routers, ZBFW, IDS/IPS, Data Probes, Data LEDs, TAPs, etc.) are integrated with the SIEM system. The use of the entire ecosystem introduces the level of security to an unprecedented level of mantle protection, where there are no areas free from monitoring and reaction functions (defensive and offensive) are able to secure every segment and component in the network.
How ARIC SIEM helps you assess and mitigate risk
SIEM ARIC and DNC appliances enable you to identify key assets and set policies to alert you when these assets have vulnerabilities or are under attack. SIEM ARIC will generate alerts based on the risk associated with any security event recorded on the DNC device.
The significance of a given security incident depends on three factors:
How SIEM helps detect threats and prioritize responses
The following illustration shows the capabilities and related tools that SIEM ARIC provides to help you perform security management tasks in your own environment.